Easily analyze user and entity behavior for whatever your purpose.
Investigate Faster
See important activities across your SaaS enterprise without complex query languages.
Simplify Logs
Turngate cuts through the structured text so you can avoid the pain of manually comparing different logs and log formats.

Rapidly Find Security Events
Something fired in the SOC and you need to dig in to determine if it's bad or not...
Alleviate Your Concerns
Who is this user and what do they normally do? What are their entitlements? Have they changed recently? What patterns of access do they have? Have they changed recently? Turngate shows who did what (and when) in a single window.
Analyze User Behavior Faster
Look for configuration changes a user began during the time period of interest. Use Turngate to establish a normal pattern of access and see if the access pattern has changed over time.
Explore Use Cases
Use Turngate For
Phaster Phishing Investigations
Do you suspect credentials been stolen? Want to find out if those credentials re-used to access systems?
First and foremost, your job is to understand what services (and data) the attacker might have accessed with a compromised account.
Oh, Phuck
Have credentials been stolen and reused to access systems? ...ls the attacker still in the system somewhere?
Turngate helps you see configuration changes by users across all services in a single window.
Steps to Find Your Phisher
Quickly see logins across all data sources. From the presumed time of compromise, Turngate makes finding all logins faster. Find services that don't require MFA. Then seek out half-completed login attempts.
Dig deeper: find login attempts where the password was supplied but not the MFA token.
Don't forget to look for activities from non-normal IP addresses. Figure out what IPs are typical for a user, then filter out activities from those IPs..
Use Turngate For
Data Exfiltration
Could be a malicious insider, could be a compromised account. Regardless, the attacker is directly focused on stealing data form the organization.

Find out what happened
Has a large amount of data been copied or moved from its original location? Has sensitive data been copied or moved?
See what might be accessed
Has data been shared publicly (ie: hasn't necessarily been accessed yet but is in a position where it can be accessed)?
Look for the reads
Use Turngate to look for a large number of data reads across all services.
Examine sensitive systems
Examine access to sensitive systems. For financial, security, and administrative systems, we help you Find abnormal user behavior faster.
.webp)
Someone is poking
Someone in the enterprise with some level of access is poking around. Maybe no data has been accessed or other malicious activity, but reconnaissance is being performed.
They're digging
Is this user checking to see what accesses and rights they have? Are they poking around in places they don't normally look in? Are any specific tools in use?
It's not normal
Establish a normal pattern of access. Has the access pattern changed over time?
Maybe they're accessing a broader set of services than normal. Or traversed multiple directory stores...or used a lot of different IP addresses.
Access, denied
Do you see any authorization misses where an attempt to access a resource was denied?
Use Turngate For
Account Usage Audits
Need to reconcile a list of user accounts with the entitlements they're supposed to have?
Or what about ensuring users have been re-provisioned when they change roles or leave the org...
.webp)
List the accounts for the system
Turngate helps compare expected entitlements against existing ones. We also simplify verifying that admin functions have only been performed by service administrators.
Turngate makes onboarding and offboarding faster
For each user, we examine all services to see if access continued past termination date (or started before an employee onboarded).
Use Turngate For
Credential Loss and Breach Visibility
Have people in your org been targeted in a breach? Or perhaps your employees have credentials that were compromised by another company.
.webp)
Find out where the attacker is
Are they still in the system somewhere?
Quickly find logins for all compromised accounts
Turngate helps you look for logins across all data sources from suspicious locations in a single interface. From the presumed time of compromise to right now.
Use Turngate For
Installed Application Audits
See who's been installing what. Turngate swiftly sifts through logs to see which user has connected third-party apps to the network.
.webp)
Comprehensive view
See if any employees have installed apps that could compromise company security.
Single Interface
Verify unauthorized access without switching between tools.
Use Turngate For
Phaster Phishing Investigations
Whether you’re sure a user got phished or you’re digging into a phishing report, Turngate can help you assess if an account has been compromised and if any malicious activity has taken place.
Oh, Phuck
A phishing report can flip your day upside down. Beyond resetting credentials, you need to know if the phish was successful. Finding anomalous account access activities (say that 4 times fast) quickly helps you know your next steps.
Did they take anything?
If the account was compromised, often the attackers first step is harvesting whatever data they can get their hands on. Our visual interface lets you quickly filter down to see all large scale data access that might indicate nefarious activity.
Don’t BECome a springboard
Beyond data theft, attackers will often try to hide their tracks or otherwise change configurations to launch other attacks. Turngate provides visibility into administrative changes that would indicate a Business Email Compromise attack is underway.
Use Turngate For
Insider Risk Management
No one wants to believe that the bad guy is one of their own. Unfortunately this can sometimes prove to be true. A good security program manages against this possibility and has tooling to help support and lead to better outcomes.
Access denied
Turngate helps you see normal patterns of use and access. You’ve noticed someone in the enterprise is poking around, attempting to log-in to systems they don’t have perms to. They are also using services they have never used before. Something might be up.
Or, maybe it’s actually ok
Our tool helps you see the anomalies and know what questions to ask. For example, you might also notice that this employee is logging in from a different IP than normal. A few questions later and you’ve now determined that Sally is working from her lake house for the rest of the summer and was just setting up a new workstation and systems to make her job easier. Whew!
Uncover the truth
You’ve also noticed this user repeatedly move and download a large amount of data. They’ve also accessed sensitive information that was previously untouched for months. Your spidey sense is tingling and you may have a true incident on your hands.
Use Turngate For
Investigating Security Events
You’ve received a security alert and now need to determine its severity. Turngate can help you quickly filter against different identities and activities over time, giving you better insight as to what actually happened.

One of these things is not like the others
Our visual interface lets you easily see differences and changes in your users’ normal behaviors. The more information you have, the better decisions you can make about next steps in your investigation process.
But some are the same
Turngate lets you filter against similar types of activities so you can see what’s going on in your enterprise. If you’ve found a suspect large deletion of data and want to look for more, Turngate can help you quickly narrow down your search.
Use Turngate For
Business Process Optimization
Sometimes your SaaS environment just doesn’t operate quite the way you think it should and it might not have anything to do with security. Turngate can help your IT team troubleshoot misbehaving IT systems and get your users back on track.

Broken clients and busted experiences
SaaS environments are often a complex web of interconnections that don’t always play nice with each other. By filtering down to the events that matter you can find general bugs, diagnose misbehaving client-side software, and see users with bad configurations.
It’s not you, it’s them
Your SaaS product is acting funny but no statement has been released yet. See lots of successful logins but nothing else? It’s probably them and you should expect their status page to be updated soon.
Use Turngate For
Account Usage Audits
We don’t currently do entitlements management, but we do help you compare expected entitlements against what your users are actually doing.
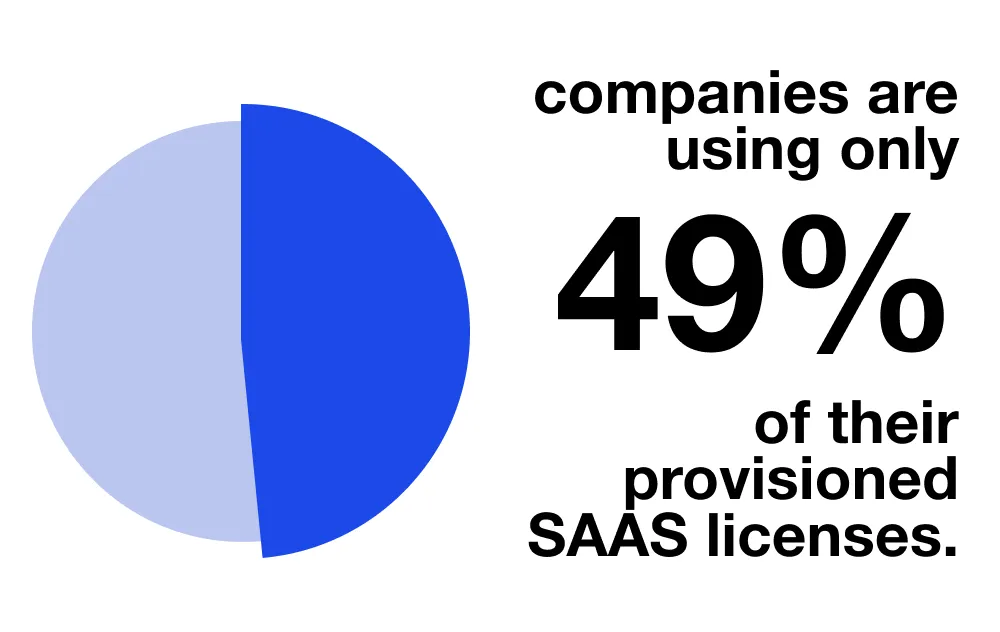
KYU (Know Your Users)
You want to make the best use of the licenses your pay for (and some of those are probably quite expensive). We make easier to see who is and who is not accessing the systems in which they’ve been provisioned. In other words, does Sally really need a developer account in Figma when she hasn’t logged into it in over six months?
Onboard and Offboard with better checks and balances
You can easily check to see if an employee’s access has continued past termination date or, conversely, started before they onboarded.
.webp)